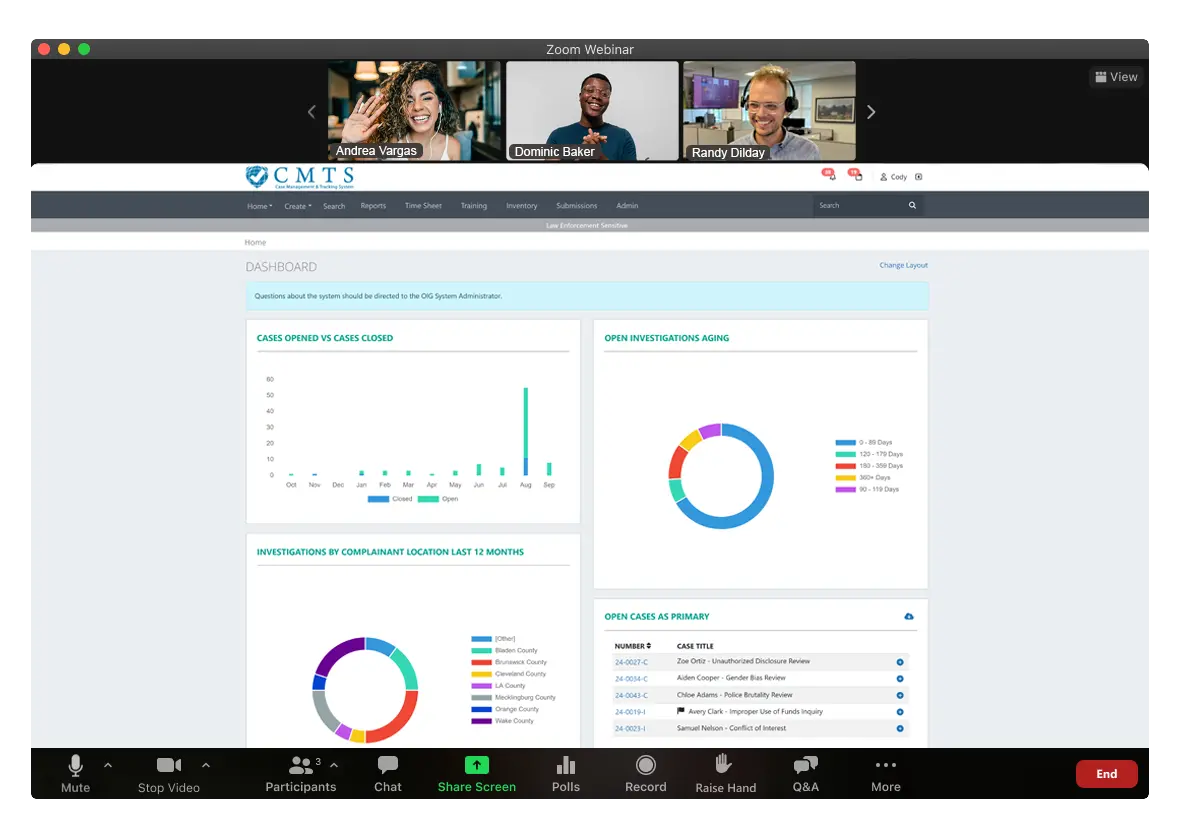
Insider Threat Investigation Case Management
CMTS empowers investigative teams to manage insider threat cases with precision, accountability, and security—built by a cybersecurity-focused organization you can trust.
When insider risks surface, the real challenge begins: documenting activity, assigning responsibility, protecting sensitive data, and ensuring compliance. CMTS helps your team do all of that—securely and efficiently.
Unlike alerting systems or cybersecurity tools, CMTS gives you the framework to respond, track, and resolve insider threat cases in a structured, compliant environment.
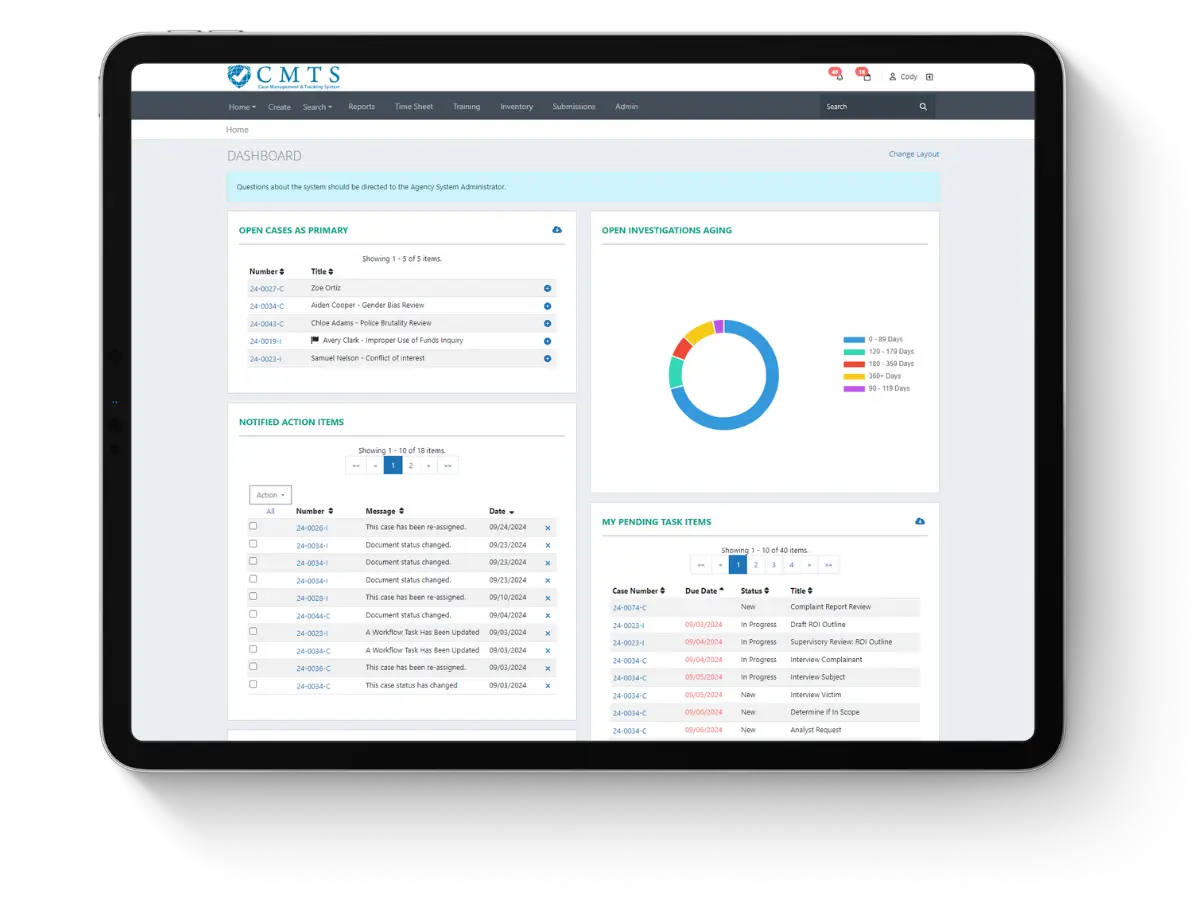
Insider Threat Investigation Case Management

CMTS empowers investigative teams to manage insider threat cases with precision, accountability, and security—built by a cybersecurity-focused organization you can trust.
When insider risks surface, the real challenge begins: documenting activity, assigning responsibility, protecting sensitive data, and ensuring compliance. CMTS helps your team do all of that—securely and efficiently.
Unlike alerting systems or cybersecurity tools, CMTS gives you the framework to respond, track, and resolve insider threat cases in a structured, compliant environment.

Why CMTS for Insider Threats?
CMTS streamlines your response to these threats by bridging cybersecurity alerts with a powerful, secure case management system. Identify suspicious behavior early, investigate thoroughly, and document every step to keep your organization safe.
Comprehensive Evidence Tracking
Preserve every file, note, attachment, and revision in a secure, versioned repository. CMTS supports detailed categorization and metadata tagging for evidence, while maintaining a complete audit history—ensuring transparency and integrity throughout every phase of your investigation.
Security in Our Organizational DNA
Developed by WingSwept, a cybersecurity-focused company, CMTS is backed by secure practices that extend beyond the software—into the people and processes behind it.

Automated Notifications & Alerts
Speed up investigations with triggers for suspicious events—like changes in user access or attempts to download classified files. CMTS notifies the right stakeholders instantly.
Integrates with Your Cybersecurity Tools
Using our robust API, CMTS integrates with tools your team already uses—SIEM, MDR, EDR, ticketing systems—to automatically ingest alerts and incident data. This turns technical signals into structured investigative workflows, allowing cross-functional teams to collaborate with clarity.

Real-Time Dashboards & Reporting
Save hours on manual data collation. Build custom dashboards for at-a-glance updates on open cases, potential risk indicators, and overdue tasks. Generate ad-hoc or predefined reports in seconds.
Configurable Workflows
From initial detection to final disposition, set the precise path your insider threat cases should follow—no coding required. Escalate complex incidents, involve HR or legal, and add steps as needed.
Robust Features For Insider Threat Case Tracking
CMTS provides a secure, flexible, and compliant case management solution tailored to meet the needs of your agency. Identify and respond to insider threats before they become critical.

Centralized Case Management
Consolidate all insider threat data, alerts, and evidence into one secure dashboard. Manage all case evidence in one secure platform, ensuring compliance and consistency in investigations.
Flexible Automated Workflows
Customize investigative processes to match your organization’s protocols and automate case progress tracking. Tailor tasks, milestones, and notifications to your exact internal protocols.

Comprehensive Evidence Tracking
Instant Reporting & Notifications
Role-Based Access Control

API Integrations
Case Management Solutions Tailored to the Needs of Your Entire Team
INVESTIGATIVE MANAGERS
Gain Visibility into Team Performance
- Instant Reports: Access case metrics in multiple formats for quick analysis.
- Aggregated Metrics: Monitor team performance and identify areas for improvement.
- Real-Time Notifications: Stay updated on case progress and critical developments.
- Time Tracking: Optimize resource allocation and ensure accountability.
- Quick Search: Retrieve case files and evidence effortlessly.
INVESTIGATORS AND SPECIAL AGENTS
Maximize Efficiency with Tailored Tools
- Custom Workflow: Adapt case progression to fit your agency's specific needs.
- Streamlined Data Entry: Focus on investigations, not paperwork.
- Personalized Dashboard: Prioritize information that matters most to you.
- Version Tracking: Maintain accurate records of documents and evidence.
- Attachment Alerts: Get notified when new evidence is added to cases.
SYSTEM ADMINISTRATORS
Simplify Implementation and Management
- User-Friendly Admin: No specialized IT training required for system management.
- Quick Onboarding: New users can ramp up swiftly.
- Flexible Hosting: Choose between On-Premise or FedRAMP® cloud options.
- Custom Permissions: Control access levels for different user groups.
- Easy Customization: Create and maintain fields to meet specific investigative needs.
Get Started with CMTS Today
Insider threats can put your organization at serious risk—don’t wait until it’s too late.
Book a call with our experts to see how CMTS can streamline your investigations, enhance security, and improve compliance.